The TOR Network : Privacy and Security at a Price

What is TOR?

TOR was initially made and implemented as a project for the US Naval Research Laboratory and was made with the sole intention of keeping government communications private. Today it has grown exponentially, maintained by people around the world, and can be used by anyone who wants to have privacy online, from people like you and me to activists, whistleblowers and journalists.
Before we proceed lets have a few definitions:
- Clearnet : This is what most people call the normal internet. When you open up your favourite browser, you are browsing the Clearnet. Here everyone knows your IP address.
- Surface Web : This is the part of the Clearnet that is directly searchable via a web browser.
- Deep Web : This is the part of the Clearnet that cannot be directly searched from a web browser. For example you can directly search for Gmail.com but you cannot directly search for a particular email.
- Darknet : Part of the internet that can only be accessed by specialized hardware, software or a combination of both. Consists of networks such as TOR, i2p and freenet.
Most people think that the Darknet is a bad place and it is mostly true. But it is not by definition bad. A direct, peer-to-peer connection between you and your friends qualifies as a darknet as it can only be accessed through the specific hardware/software configuration.
TOR is one way to access the darknet and to browse privately. It uses a network of virtual tunnels and bounces your data through separate relays.
How does it work?
TOR works by using a network of TOR relays. Instead of directly connecting to the resource, like in the Clearnet, TOR sends the data packets through several relays. The number of relays is hardcoded to 3. Each relay knows where the data is coming from and where is going, nothing more. It doesn’t even know what the data is as it is encrypted.
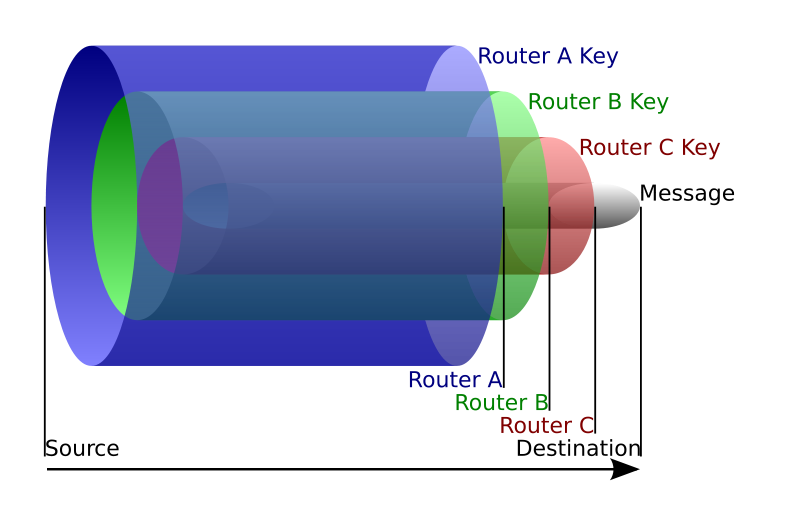
The data is wrapped up in 3 levels of encryption before transmission. The data can only be fully decrypted at the endpoint and the destination resource sends its response, which is also encrypted, through the same tunnel that lead to it and is decrypted fully by the user.

Once the data is wrapped, it is sent from the TOR browser to the Entry Node. This is where the data enters the TOR network. The entry node decrypts the first layer of encryption in the data and this tells it to send the data to the next relay node. This relay node decrypts the second layer, which tells it to send the data to the last node in the TOR network, the exit node. This is where traffic from the TOR network surfaces to the normal internet. The exit node decrypts the last layer and sends the data packet to the destination resource. The 3 relays, in short, peel off the layers of encryption like layers in an onion, hence the name. The resource’s reply would also arrive to the user in a similar manner. The 3 nodes/relays can be situated in different parts of the world and the route the data takes through the TOR network is chosen randomly and is changed in certain intervals. The entry and middle nodes do not know the destination of the data and the middle and exit nodes do not know the source of the data. Anyone can start a TOR relay.
This system is very secure and prevents websites from finding your location. The use of 3 different relays that are located in 3 different parts of the world and maintained by 3 different people or organizations prevent even the relays from learning about you. Even you internet service provider won’t know what you are doing in the TOR network if you are careful. You can use TOR to reach any part of the internet, effectively fighting against things like government censorships.
Now don’t get me wrong, TOR can be used to access many illegal sites in the darkweb and the less known about what’s happening on those sites the better. But it is used for good purposes as well.
TOR is well known in the news as things like the Edward Snowden leaks and the Collateral Murder videos were sent through TOR.
But what is the price of all this security? Speed. Obviously sending encrypted data through 3 relays and getting the reponse back takes a lot of time and playing videos are out of the question, but perhaps it is a necessary and reasonable price to pay.
TOR provides a platform for journalists to communicate with whistleblowers, for activists to let their voice be heard, for whistleblowers to let the public know distrubing truths, for people to resist government censorship, for victims of rape to communicate with welcoming communities and for people to communicate with law enforcement securely. For them TOR is not just a browser. It is a necessity and a way of life.
References: