Hashes And Hashing Algorithms : A Primer
Hashes are generated using hashing algorithms. These algorithms take an input, for example a password, scrambles it and then returns a fixed length output, the hash.
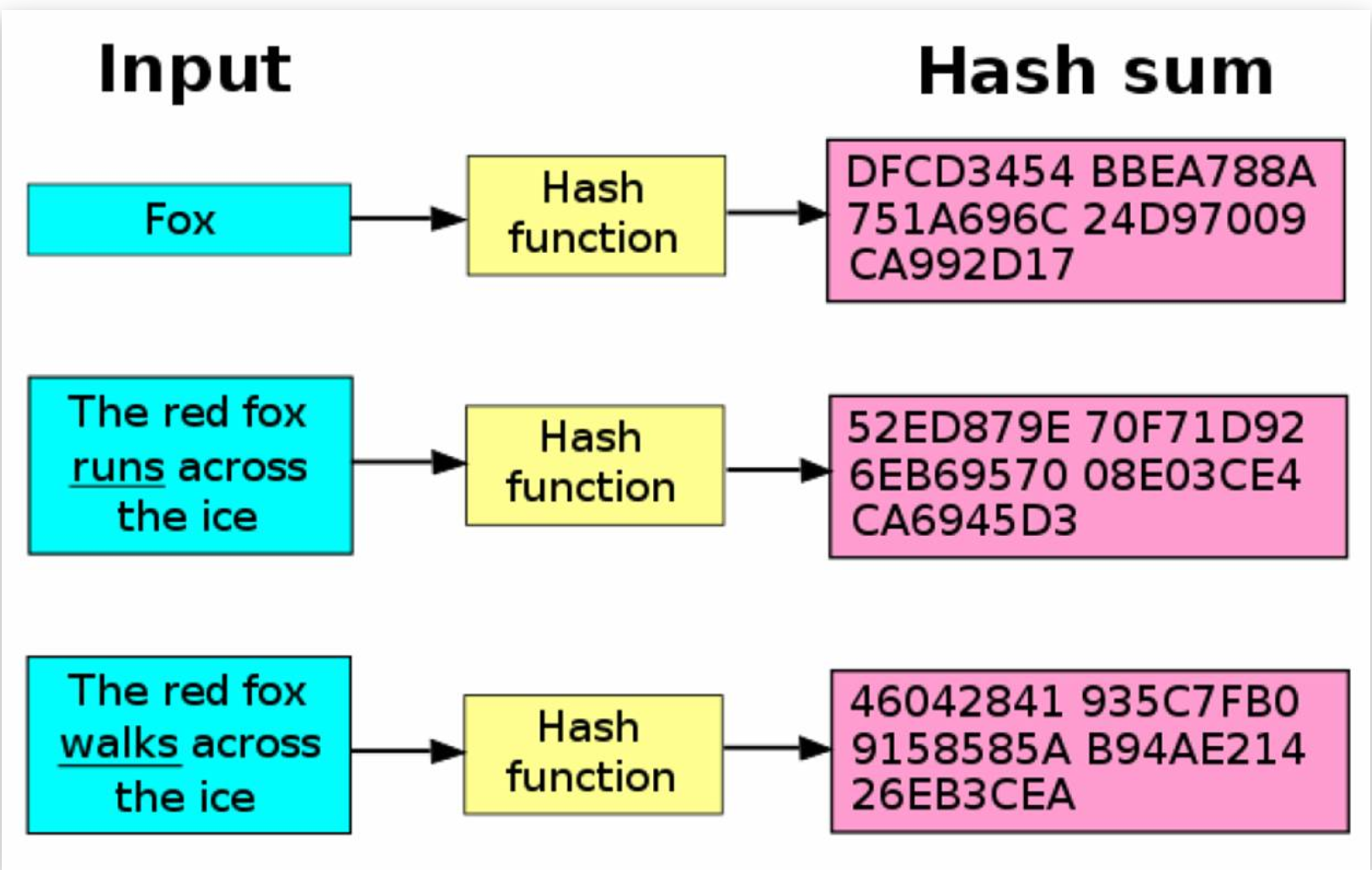
Looking at the above image you can clearly see that even a small change to the input can result in a completely different hash. Hashing algorithms are designed in such a way that even small changes to the input will drastically alter the hash.
Figuring out the original input when you have the hash output is generally difficult but the algorithm can generate a hash quickly.
So what are hashes used for?
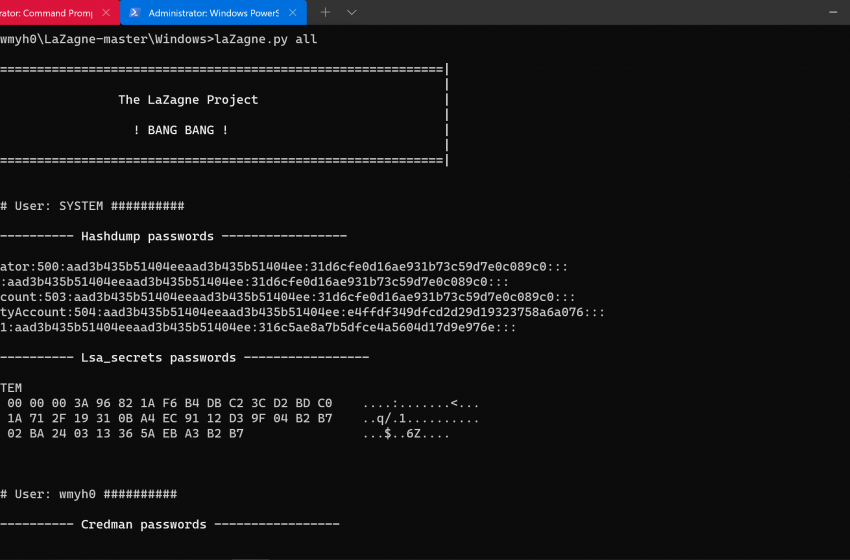
Hashes are used extensively in encrypting and storing most passwords. The recent Windows operating systems use the New Technology Local area network Manager(NTLM) suite to hash and store login passwords. Your login password that is stored in your Windows pc might look like :aad3b435b51404eeaad3b435b51404ee.
They are also used to verify the integrity of files. Some sites provide the hash of the file they distribute. The user can download the file and use the hashing algorithm on the file. If the hash produced by the user and the hash provided by the distributor is identical, then the file has not being corrupted. If they are different then there is an accidental or malicious change in the file.
Another use for hashes is hash tables. These tables are used as a form of rapid data retrieval. These hash tables are used by search engines to index and rapidly lookup webpages.
Some examples of popular hashing algorithms include MD5(Message Digest algorithm 5), SHA(Secure Hashing Algorithm), AES(Advanced Encryption Standard), and more.
So can hashes be broken or cracked? Yes, absolutely. There are several methods used to crack hashes. One way is the Dictionary attack. As the hashing algorithm is known we can generate the hashes of a list of input texts from a file, the ‘dictionary’ and compare the hashes with the hash we want to crack. Another method is called the brute-force attack. If we want to crack the hash of a password we can try the hashes of every possible password. The software will compare the hashes while they are being generated, with the original. This method would guarantee that the hash will be cracked but depending on the complexity of the original input, brute-forcing a long complex password may take an unreasonable amount of time.
There are several software available to crack hashes. Some of them are Ophcrack, John the Ripper and Hashcat. Hashcat is available in Linux and Windows platforms and can use a computer’s graphics processing unit to rapidly generate and compare hashes. John the Ripper is another software used to crack hashes but is only available in Linux platform.
So that is what hashes are and frankly they are a great thing as they provide us with a reasonable amount of security.